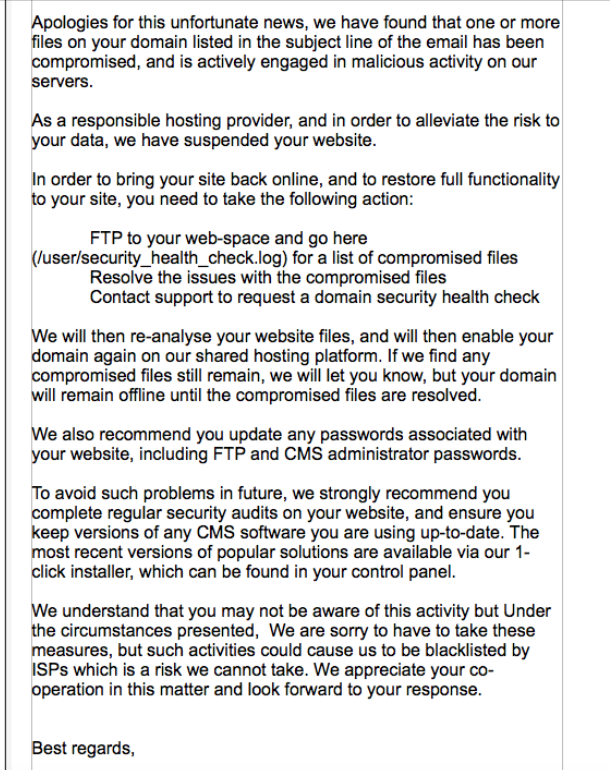
My client got every web owners worst nightmare when she received this email from her hosters, telling her that her website had been taken offline for containing malicious files:
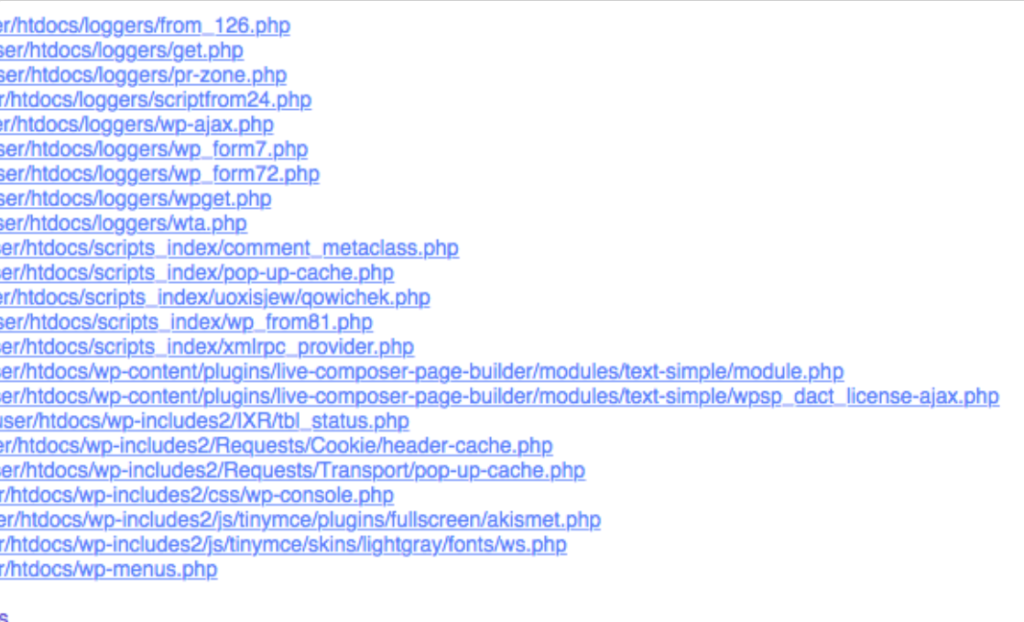
They sent a list of suspect files, most of which look innocuous and can hide easily in a WordPress installation:
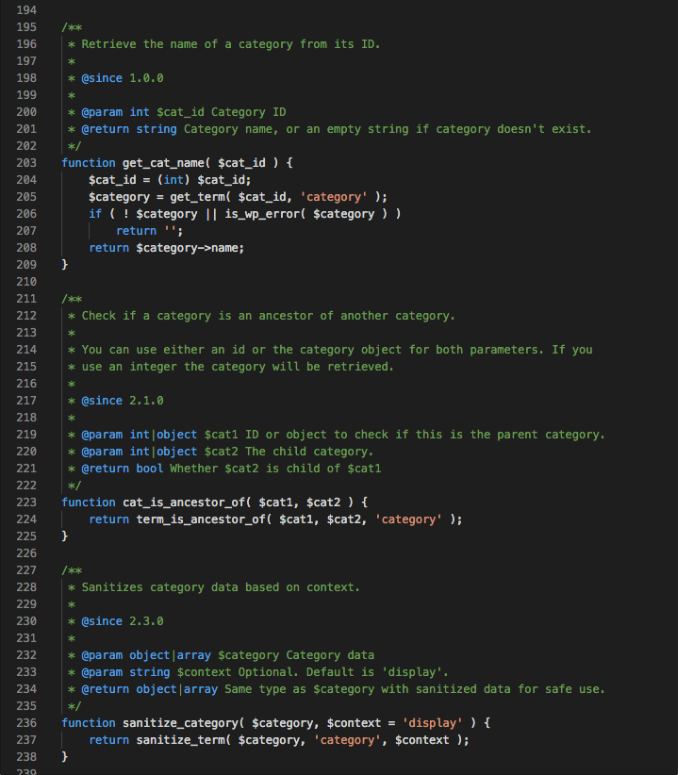
Going through the files, it was clear straight away that most were malicious. This is legitimate WordPress core code, clean and well-commented:
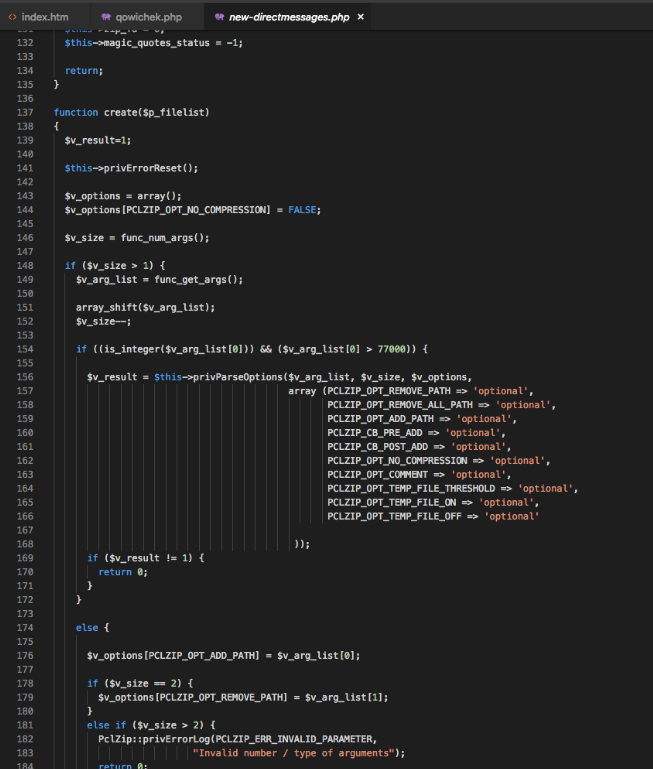
And this is malicious code from her site, which isn’t so pretty and contains little clue as to what it’s meant to do.
Many of the files were also encrypted:
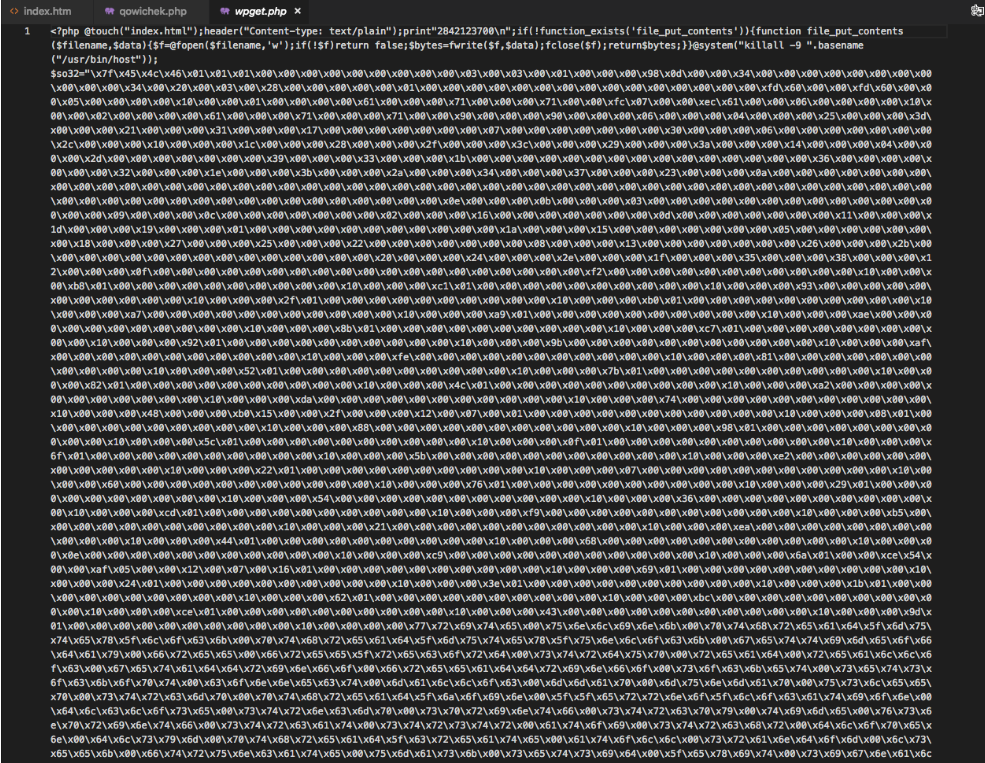
The most interesting ones though, gave a clue as to why the site had been hacked. There were over 700 files containing content for junk ads and popups and templates to display them in. These are just a few:
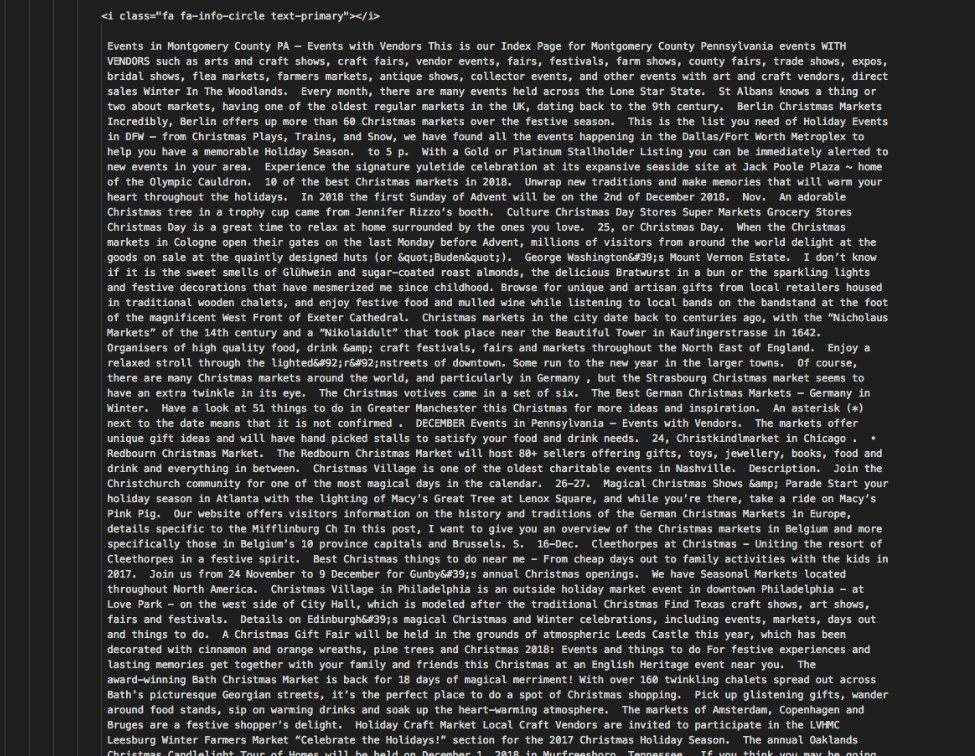
Opening up these files gave us advert content, such as this one for Events in Montgomery County
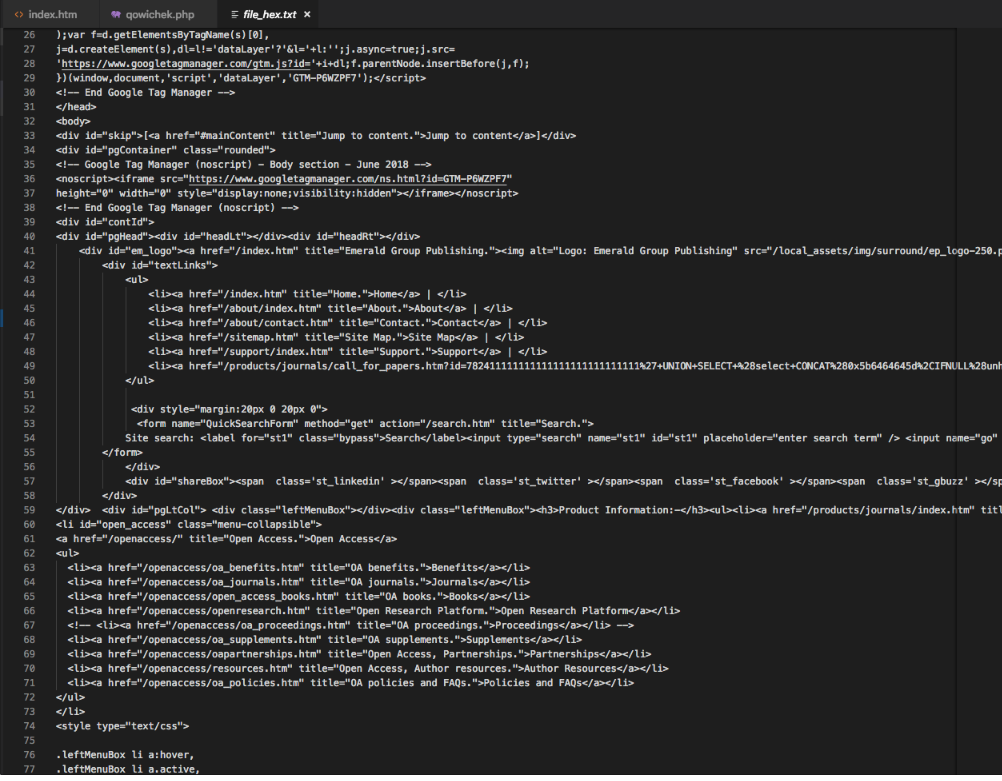
Or complete web pages, such as this one for Emerald Group Publishing
But it got better. The hackers had left their calling card in the code. I even managed to find their website online (and quickly left)
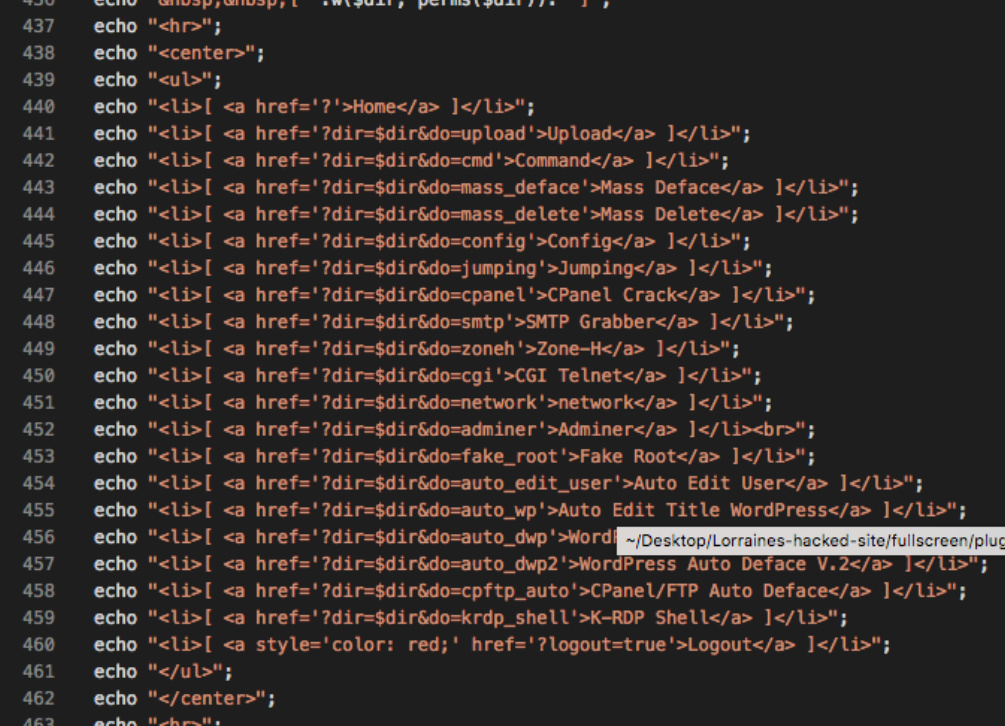
This page is a control panel with options to delete or deface your website, and hijack your mail server or your CPanel. There was also code to check for every main eCommerce provider’s database tables and harvest your customer information.
What I did
I started out trying to prune the infected files from the good ones, but hackers leave ‘back doors’ in the code, meaning if one file is deleted it will automatically be re-uploaded. I deleted around 800 files the first day. The next day 400 of them were back again.
It seems this had happened as a result of an already dormant back door as the client had been brute-forced 6 months before and the hosters had “fixed” it (by creating a clean installation of WordPress but leaving all the old files on the server).
There was no damage to her child theme or to the database, so instead I wiped the entire server, reinstalled a clean installation of WordPress and re-uploaded her child theme. We changed the login screen location and installed anti brute-force lockout software, and since then no problems.
How to Protect your WordPress Installation
It’s common to think no-one wants to hack your website, but the very fact you’re on a server means that server is useful to hackers, for sending junk emails, popup ads, harvesting your database, or mining bitcoin. The very fact that you’re using WordPress also makes you a target.
No-one is sitting in a little room somewhere “hacking” your site. Hackers write software that will make its way around the web looking for WordPress installations, then trying the easiest ways in. Once the program gets in, it will notify the hacker and start looking for all the obvious ways into your database, server and SMTP server. You’re not being specifically targeted, hacking software is opportunistic and goes for low-hanging fruit.
To hang your fruit a little higher, these are the main things you can do:
- Install the best security plugin you can to prevent brute-force attacks and monitor for malicious-looking files.
- Install all updates immediately. Once an exploit has been identified hackers update their software and the code authors remove the exploit. If the hackers get there before you update and remove the exploit they’ll get in.
- Don’t let your login name be the same as your published name, or anything like ‘administrator’ or ‘admin’.
- Move your wp-login screen to a custom location.
- Use strong passwords that won’t be brute-forced
- Don’t use wp_ as your database table prefix
- Run integrity checks on your WordPress core to look for non-standard files (this is also useful if you believe a lazy developer might have hacked your core).

